How to Block Ads on Your Internet - 2024 Edition

There are countless ways to block ads today, depending on where in the connection process you choose to intervene. This guide begins with a straightforward 5-minute ad-blocking solution, and follows with some more advanced techniques for the self-hosters. I'm prioritizing solutions from the sea of options that are open source, easy to set up, low impact, and privacy-protecting.
For a quick solution, jump down to the setup portion of this post. Or, keep reading for an overview of ad-blocking techniques and how I have my own setup configured. I've been dodging advertisements on the web since I realized I could. If given a choice, I'd prefer to watch TV without commercials, just as I prefer to explore the web without sales, deals, and feeling like everyone sees me as a conversion. I know there's been great effort put into the notion of acceptable ads -- but these are not yet acceptable solutions to me. Website admins who responsibly curate and reign in which ads are allowed on their sites are few and far between. An internet where ads aren't awful (surveilling, bandwidth-intensive and distracting) is still a place where sales pitches hide within content. Everyone has different reasons to block ads, but mine are:
- In the real world, I don't like strangers walking up and telling me to buy something
- I can't individually analyze what makes an ad or its properties acceptable and unacceptable
- I can't keep up with which ad networks do or don't sell data to third parties around the world
Blocking Ads is not just about removing annoyances #
Over the years, ad networks have faced significant criticism for their poor oversight, leading to the frequent distribution of malware and the facilitation of disinformation campaigns. In 2016, major websites like The New York Times and BBC were hit by “malvertising” attacks, where malicious code was delivered to users through compromised advertisements served by legitimate ad networks. During the 2016 U.S. presidential election, Russian operatives exploited ad platforms on Facebook and Google to disseminate disinformation aimed at influencing voters. Just last month, reports have surfaced about Google AdSense ads spreading conspiracy theories against muslims in India following the country's deadly floods. These examples illustrate the persistent challenges ad networks face in monitoring and controlling the content they distribute, often making them the tip of the spear for malicious activities online.
Because of this landscape which has accelerated and become even more toxic over the past five years, I decided to devote some time figuring out how to filter these ads. I've toyed with everything from powerful open-source DNS servers to fun homelab hardware projects, and with all these experiments in mind, I’ve landed on one recommended ad-blocking technique. For protection comparable to premium services or complex local DNS server setups, I recommend using Mullvad’s free DNS servers. Their servers handle ad blocking, managing lists of ad servers and trackers, and simplifying the process for you. Here's Mullvad's help page about their DNS service. Once your block is in place, ads are replaced by clean empty spaces, and typically the webpage adjusts seamlessly, shrinking the ad block into oblivion.
How to set this up: #
Here's the basic setup I suggest for most people looking to easily block ads:
- Force your browsers and devices to use the Mullvad DNS service (see set up instructions for various devices below)
- Use Firefox with the Ublock origin extension
- If you're hooked on Chrome, UBlock Origin Lite works well enough, but you can also force Chrome to use the Mullvad DNS too.
- For your home router, use the 'Base' Mullvad filter too.
Jump to how to set this up for your router + browser + mobile device.
Here’s how to set up Mullvad's base filter by ensuring our devices use it:
Setup your Router #
Because all device requests in your home pass through your router (the device your modem connects to), a great first step is to set this up to block ads. Start by following these instructions. For routers supporting DoH (DNS over HTTPS), then you can drop this DNS server in: https://base.dns.mullvad.net/dns-query -- otherwise, you may need to change your DNS server on your browser. If your router does not support DoH, you may want to use one of the regular IP addresses for the ControlD service, which also provides a free ad blocking DNS service. Requesting DNS over a regular IP address is less secure, however.
You'll also need to set up device-level DNS protection, because browsers use their own default DNS resolver instead of inheriting from your router. So, in addition to router setup, also install Ublock Origin on your browsers (Ublock Origin Lite on Chrome) and use the Mullvad mobile config on iOS/Android as described below.
Your Browsers Need New DNS servers, too #
Chrome's settings define its own DNS universe and will need a new DNS server too. Here's how to update it. Use this URL: https://base.dns.mullvad.net/dns-query
Firefox also has its own DNS settings which can be updated by searching for DNS in the Settings, and choosing 'Max Protection', choosing a custom server, and using the Mullvad DoH URL: https://base.dns.mullvad.net/dns-query
Setup on iOS / Macs #
For Apple devices, you can use a 'mobile device config,' which Mullvad has created and signed for security to ensure all DNS requests go through Mullvad instead of your mobile network provider or your router's default. Grab one here for the 'base' blocklist. All this mobileconfig does is say "Use Mullvad DNS" on all devices it's installed on.
Installing this mobile config on either a Mac or iOS device means you're using only Mullvad's DNS for all queries, and Mullvad uses these filters.
Here's how to install this file on an IOS device and here's instructions for a Mac.
Android? #
For Android, follow these instructions:
- Open Settings on your Android device.
- Go to Network & Internet.
- Select Private DNS.
- Choose Private DNS provider hostname.
- Enter the following:
base.dns.mullvad.net - Save the changes.
Windows #
Read this to setup Mullvad DNS on Windows.
Let's Test: Are the ads blocked? #
Once you get all setup, you can test whether your ads are actually being blocked by visiting this page which tries to connect to a huge list of ad servers: https://d3ward.github.io/toolz/adblock and https://adblock-tester.com. Or, just go to a website which has annoyed you in the past. On a mobile device, try opening your favorite news website app -- since DNS filtering happens at a lower level than browser plugins, you should see ads blocked even in apps.
You should see something like this on the d3ward test without any protection:
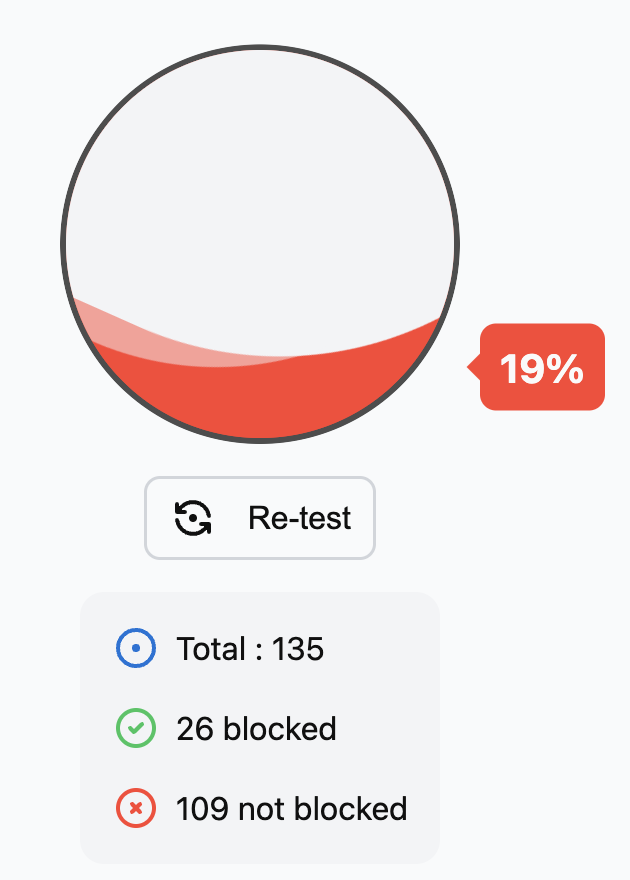
And with just the Mullvad DNS server, you should see:
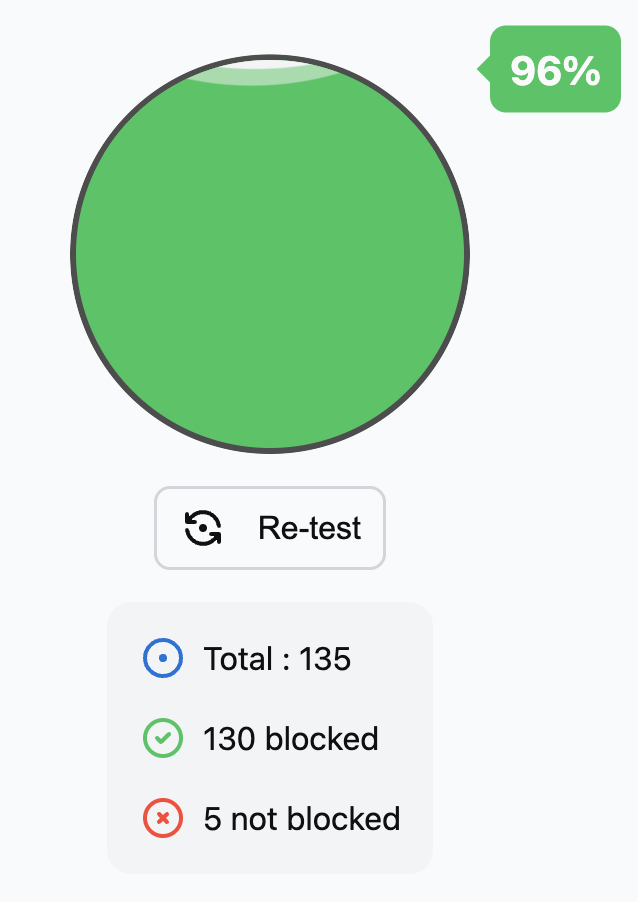
Device-level DNS filtering blocks ads even in places like the New York Times app (which appear despite being a paying subscriber).
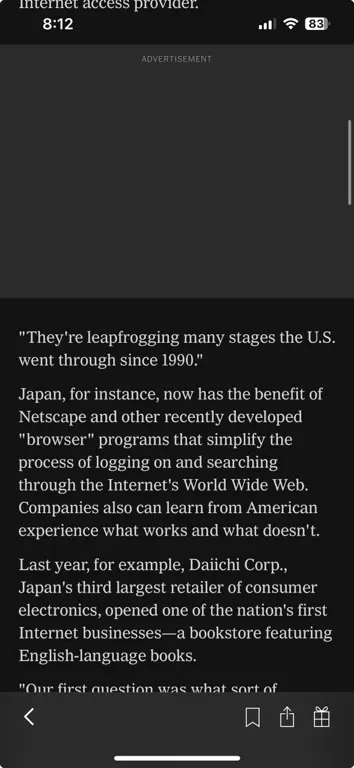
One simple change to your DNS settings can have a significant impact on your browsing experience. Starting with a DNS-first setup is a great way to get excellent base level blocking. You may not even need an extension. By avoiding ad-blocking extensions that frequently download filter lists (already handled by Mullvad), you save bandwidth and experience faster browsing. Ad-blocking extensions use significant CPU resources to maintain lists and parse content.
How Mullvad DNS works: #
Here's a quick overview of how Mullvad's DNS servers work. When connecting to the internet, your device queries the Domain Name System (DNS): 'Where can I find this website?' Your DNS server responds with the site's IP address such as: '189.122.221.1'. When loading content from that server, advertising, tracking, and other unnecessary servers are contacted as well. A DNS server which knows 'This is an ad server' and 'This is a news website' is incredibly valuable, because it enables you to only load the content from basedomain.com and not the ad content from adserver.elsewhere.net. This ensures that your computer will not load advertising content or ping tracking domains.
Massive lists of domains that host ads, tracking software, malware are maintained by volunteers. FilterLists is the place to peruse these lists. Having these lists compiled makes it easier for ad-blockers to effectively target advertising content.
Here are a few of the bigger, and most actively updated lists, which each haveones with a long history and frequent updates:
If you have a few days to burn, you could dig into how these lists are built, when they're updated, and build your exact shield like a wild alchemist. But life is short, and working to discover and block advertising domains could be a full-time job. Rather than doing this labor yourself, trust that Mullvad has curated an effective ‘Base’ list to do the heavy lifting for you.
Here's how to use the 'base' Mullvad dns servers.
Lists are the key: a living list of blocked domains who have wronged people (hosted ads) #
Lists like OISD and the StevenBlack hosts list aggregate multiple blocklists. For OISD's case, you can see the source list here. The 'BIG' OISD list is indeed big, and clocks in around 176Kk individual domains and updates daily. Mullvad uses a curated and safe 'base' list which includes a pared down version of OISD called oisd-small, which they’ve optimized for safety and minimal false positives. It also passes the 'grandparent' test, meaning it won't break webpages.
Why Mullvad? They're independent, operate under Swedish law (here’s why this matters), and work hard to find ways to protect privacy. A couple of years ago they removed recurring subscriptions for their VPN to avoid storing data about users! Their work on Defense against AI-guided Traffic Analysis (DAITA) is worth reading about.
Home Routers Part 2: The Homelab Approach #
If you want to manage your own lists, you can set up an Adguard or similar homebrew ad blocking DNS server on a Raspberry Pi, old PC, or virtual machine. Let's say you have a LG tv, and you don't want to see ads on its terrible menus. Subscribing to this smarttv blocklist, for example will make sure the following long list of domains are blocked by your, say, LG tv and any other tv brands you can imagine:
# LG
ad.lgappstv.com
ibis.lgappstv.com
jp.rdx2.lgtvsdp.com
jp.lgtvsdp.com
jp.info.lgsmartad.com
lgad.cjpowercast.com.edgesuite.net
#ngfts.lge.com # blocks thumbnails from loading in the LG Content Store
smartclip.com
smartclip.net
smartshare.lgtvsdp.com
us.ad.lgsmartad.com
us.ibs.lgappstv.com
us.info.lgsmartad.com
#us.lgtvsdp.com # #117
us.rdx2.lgtvsdp.com
yumenetworks.com
aic-ngfts.lge.com
us.cdpbeacon.lgtvcommon.com
us.cdpsvc.lgtvcommon.com
us.homeprv.lgtvcommon.com
us.nudge.lgtvcommon.com
us.rdl.lgtvcommon.com
us.recommend.lgtvcommon.com
us.lgsmartad.com
us.service.lgtvcommon.com
If LG comes up with new domains to host their ads on, this filter maintainer will add them. SmartTV's don't just show ads, they track and analyze schedules, behaviors, and tastes. This thesis from 2020 on data collection by five smart TV vendors found that even if a privacy policy is declined, personal information is still sent to third parties.
A consumer who disagrees with Smart TV’s privacy policies, naturally assumes that no PII will be collected. However, not only will the consumer lose Smart functionality, but the PII metadata is still collected and sent to the vendors. This research shows how Smart TV manufacturers are not necessarily aligned with their own policies. (page 93)
There are two home routers systems that really nail the adblocking experience. Firewalla in particular goes above and beyond and looks at the behavior of your devices to detect malware, and Gl-inet let's you run Adguard, a filtering tool that lets you pick and choose your own blocklist recipes:
- Firewalla. Firewalla is my top choice, since it's extremely user friendly and lets you isolate individual devices but it does require a wifi access point. Their default adblocking works well and you can also use the OISD list.
- Gl-inet. Right now the GL-AXT1800 is the best bet as an all-in-one solution. I bring this with me on trips and just plug it into an internet source.
Adguard appears to be the new favorite over PiHole so I'd recommend setting up Adguard on the GL-inet router for a simple yet powerful adblocking solution if you want to create a quick set it and forget it home network with filtering.
So what are my Lists #
After digging a little into lists, here's a few I've chosen:
| Name | URL | Count (as of 9/2024) |
|---|---|---|
| AdGuard DNS filter | link | 67,573 |
| Phishing URL Blocklist (PhishTank and OpenPhish) | link | 439 |
| Dandelion Sprout's Anti-Malware List | link | 24,835 |
| ShadowWhisperer's Malware List | link | 47,564 |
| Malicious URL Blocklist (URLHaus) | link | 1,606 |
| The Big List of Hacked Malware Web Sites | link | 13,468 |
| Perflyst and Dandelion Sprout's Smart-TV Blocklist | link | 159 |
| Smart-TV Blocklist for Pi-hole | link | 242 |
| WindowsSpyBlocker - Hosts spy rules | link | 347 |
| uBlock filters – Badware risks | link | 3,026 |
| HaGeZi's Threat Intelligence Feeds | link | 724,491 |
| Dandelion Sprout's Anti Push Notifications | link | 506 |
| Dandelion Sprout's Game Console Adblock List | link | 11 |
| HaGeZi's Pro++ Blocklist | link | 184,523 |
I've customized my above list to block Smart Tv advertising, console ads, malware, and Windows-specific tracking.
As operating systems, consoles, and devices evolve, I have faith that the filter maintainers I subscribe to will continue improving coverage while limiting false positives. By using multiple reputable filter sources, this setup casts a wide safety net while avoiding overblocking legitimate content. The best part is it updates daily.
That's about all I've got -- I'll update this next year!
Let me know if you need any help with your adblocking setup.
by Daniel Morgan, tagged with: ads, selfhosting
